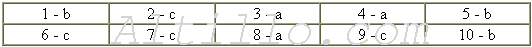
Altillo.com
> Ex�menes > CAECE
> Systems
| Systems | 2� Examen | Mayo de 2001 | Altillo.com |
TEXT ONE
A) Please read this text:
Wireless networks leave computers open to "drive-by" hacking - Will Knigh
A string of weaknesses with the security infrastructure protecting wireless computer networks have been highlighted by researchers at a major computer security conference in the US.
The problems have been identified with the 802.11 set of specifications created by the Institute of Electrical and Electronics Engineers for wireless local area networks.
Wireless networks are growing in popularity. However, experts have described ways to eavesdrop on wireless traffic, intercept communications and even gain full access to such a network.
"As 802.11 wireless networks become more common, companies' intranets are increasingly being exposed to drive-by hacking," said Dave Safford, manager of network security research at IBM.
Information on these vulnerabilities was presented on Friday at the Black Hat Conference in Las Vegas. This is the most high-profile US meeting of legitimate computer security experts and underground computer hackers.
Stream cipher
The wireless specification known as 802.11 is protected with a system called
Wired Equivalent Privacy (WEP). Communications are encrypted with a stream
cipher, meaning that each bit is altered according to a secretly held key during
transmission. There are a number of rules designed to ensure that keys are used
securely and no one can eavesdrop on messages.
But Ian Goldberg, chief technical officer for Canada's Zero Knowledge systems, presented fundamental flaws with the implementation of the encrypting rules that leave 802.11 communications vulnerable.
He described ways to monitor wireless network traffic in order to gather information about how messages are encrypted. Given this, he says it is possible to modify and even decrypt communications altogether.
Multiple guess
Another conference delegate built on these vulnerabilities to describe
practical methods of attacking 802.11 networks. Tim Newsham, a consultant with
US security firm @Stake, outlined a technique for decoding messages by testing
out a series of cryptographic keys at high speed. Further research indicates
that networks using encryption that cannot be cracked in this way may still be
vulnerable to automated password guessing.
"WEP is inherently insecure," Newsham said. "So using WEP is essentially just throwing another barrier in front of the attacker."
Another computer security expert, Mandy Andress of ArcSec Technologies, described how unprotected wireless networks can be attacked in many real situations by roaming hackers.
Ollie Whitehouse, a computer security expert with @Stake in the UK says that research in this area is likely to increase investment in wireless security. "There are flaws that require modification and I think you will also see people investing in larger encryption keys and incurring the computational overhead," he told New Scientist. The first industry steps to secure the standard have already taken place. IBM has developed software for a wireless handheld computer that will automatically alert a user to potential vulnerabilities in a particular 802.11 network.
Now say if these statements on the text are True or False:
1. Researchers at the conference said wireless networks are not safe
................ True - False
2. The 802.11 specifications were written by wireless networks users
............... True - False
3. A lot of people are using wireless networks
.................................................. True - False
4. Legitimate experts and illegal hackers meet at the Black Hat Conference
....... True - False
5. Communications encrypted with a stream cipher are supposed to be safe ......
True - False
6. Ian Goldberg thinks 802.11 communications are vulnerable
........................... True - False
7. Newsham contradicted Goldberg
................................................................. True - False
8. Encryptions that are cracked in the way Newsham explained are vulnerable ...
True - False
9. Mandy Andress is a real roaming hacker
....................................................... True - False
10. IBM has developed software to protect users from hackers
........................ True - False
Now answer, please:
1) The word "highlighted" (line 2) suggests that .................
a) the speakers were using colour pencils.
b) researchers put special emphasis on this idea.
c) researchers were the stars at this congress.
3) The Black Hat conference has a high profile. In other words, it is
...................
a) very expensive.
b) prestigious and famous.
c) broadcast by TV.
4) "... secretly held... "in line 21 means that ...................
a) nobody knows that this key exists.
b) it is difficult to find this key.
c) a person presses this key during the operation, but nobody knows about it.
5) "... in order to ... " in line 28 is used to express ...........
a) condition.
b) purpose.
c) opposition.
6) "Further .... " in line 36 means ....
a) later research.
b) more complex research.
c) more research.
7) In ".... by testing out .... " in line 35, the preposition
"by" is used to express ....
a) the method they used.
b) what they were doing at the moment.
c) the author.
8) In "... a computer security expert with @Stake.. ", the
preposition "with" denotes that ....
a) this man is the owner of the company.
b) he works for that company.
c) he uses @Stake.
9) The word "flaws" in line 46 refers to ..........
a) problems with the security experts.
b) changes to the encryption process.
c) problems with wireless networks.
10) A handheld computer is one which ..........
a) is user-friendly.
b) is very handy, good for many jobs.
c) is small enough to be rested on one�s hand.
TEXT TWO
A. Please read this text and answer the questions below it:
IBM INTRODUCES COMPUTERS TO EASE INTERNET COMMERCE
International Business Machines introduced a
revamped line of computers that are aimed at making it easier for small and
medium sized companies to do business on the Internet.
The IBM AS/400e series of computer servers, with two times the storage
and five times the memory of previous models, is backed by World Wide Web
programs and has increased Internet security. It's also designed to ease the use
of different software programs and languages like Java, Lotus Domino and ActiveX.
The computers use new 8-way and 12-way processors. They use a new release
of the OS/400 operating system designed to maximize performance according to the
users' needs. The machines are divided into two series of models. One designed
for interactive processing and another optimized for batch processing.
The enhanced security features include a "Firewall" that
controls user access to the Internet as well as protecting non authorized users
of the public network from using the resources of the internal network.
IBM and other companies are seeking to provide servers, which manage
networks of PCs, and computers that make it easier to conduct business over the
Internet. Business to business commerce over the global network is expected to
rise to 327 billion in 2002 from eight billion this year according to research
firm Forester Research.
B. Say if these statements are True or False:
1) This is a series of modernized and modified computers .......... True �
False
2) These computers are completely new .................................... True
� False
3) You can store much more information in these computers ...... True - False
4) World Wide Web has nothing to do with these computers ..... True - False
5) The languages mentioned here will be unnecessary ................. True �
False
6) Servers are larger computers
................................................. True � False
7) The OS/400 will be adapted to the users' needs ..................... True -
False
8) "Firewall" is used for protection
............................................. True - False
9) IBM does business only with PC networks ............................ True �
False
10) Forester expect the global network to grow ......................... True
� False
TEXT THREE
A. Jigsaw reading. Set the pieces of this text in order: Put
numbers in the rectangles.
Searching with Quantum Computers
A high-speed quantum algorithm for exhaustive searching
By Lov K. Grover


VOCABULARY
TICK THE CORRECT WORD:
1. With the .............. of the computer, business changed.
a. invent b. advent
c. inventing
2. I don't want to ................. about this. I want
practical solutions.
a. theory b. theoretical
c. theorize
3. The ................... of a new system of accounting was
very important.
a. development b. develop
c. developing
4. Computers were possible after the ............... of the
thermionic valve.
a. discovery b. discover
c. discovered
5. This new system .............. from the old system.
a. evolution b. evolved
c. evolving
6. This ..................... is very important for analyzing
the financial conditions of a company.
a. apply b. applicant
c. application
7. Accountants are fundamental for the ................. of
our operations.
a. succeed b. successful
c. success
8. My secretary is irresponsible. She is not
...................
a. reliable b. rely
c. reliance
9. We are going to make an ............. and buy new
computers.
a. invest b. investing
c. investment
10. This product is very expensive. It does not have a
............... price.
a. competition b. competitive
c. compete
Respuestas
Text One
Ejercicio b)
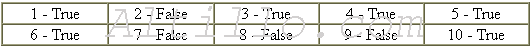
Ejercicio c)
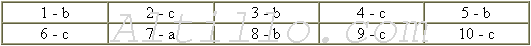
Text two
Ejercicio b)
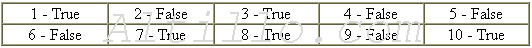
Text three
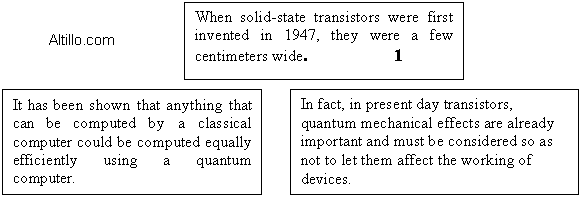
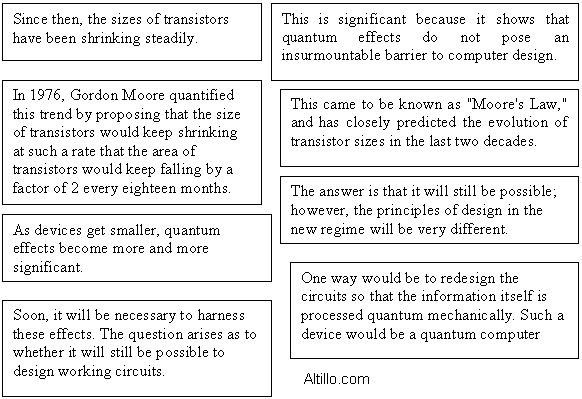
Ejercicio a) When solid-state transistors were first invented in 1947, they were a few centimeters wide. Since then, the sizes of transistors have been shrinking steadily. In 1976, Gordon Moore quantified this trend by proposing that the size of transistors would keep shrinking at such a rate that the area of transistors would keep falling by a factor of 2 every eighteen months. This came to be known as "Moore's Law," and has closely predicted the evolution of transistor sizes in the last two
decades.
As devices get smaller, quantum effects become more and more significant. In fact, in present day transistors, quantum mechanical effects are already important and must be considered so as not to let them affect the working of devices. Soon, it will be necessary to harness these effects. The question arises as to whether it will still be possible to design working circuits. The answer is that it will still be possible; however, the principles of design in the new regime will be very different. One way would be to redesign the circuits so that the information itself is processed quantum mechanically. Such a device would be a quantum computer. It has been shown that anything that can be computed by a classical computer could be computed equally efficiently using a quantum computer. This is significant because it shows that quantum effects do not pose an insurmountable barrier to computer design.
Vocabulary